Securing your Salesforce Org
Ensuring your Salesforce org is secure and keeping up with the ever-evolving security landscape can be a challenging balancing act. To protect customer data, Salesforce will be requiring customers to set up Multi-Factor Authentication, MFA for short, for all users logging into Salesforce through the user interface.
If you aren’t currently using MFA, there’s still time! Salesforce will begin auto-enablement starting this fall (September and October) so you’ll want to make sure there’s a smooth transition. We’ll discuss more on this below.
Note: Current roadmap shows enforcement beginning in 2023.
The good news is that MFA is available at no extra cost and Salesforce offers several options for verification. Let’s dive in and learn more about it.
What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) is an authentication method that requires users to present two or more pieces of evidence-or factors-in order to log in.
Previously, Salesforce would speak of 2FA (Two-Factor Authentication), but now we’re focused on MFA (Multi-Factor Authentication). The difference being that MFA provides functionality supporting two or more factors, whereas 2FA supports two factors only.
What is the benefit of using MFA?
MFA is an effective and easy way to increase protection for user accounts against common threats like phishing attacks, credential stuffing, and account takeovers. By requiring multiple factors to authenticate upon login, a Salesforce Administrator can ensure a more secure org and protect their business and data against security threats.
What are Factor Types?
Factors refer to the ways that you can authenticate yourself in order to login. These factors can consist of
- Something you know: username and password
- Something you have: a physical object such as a security token (USB) or key
- Something you are: physical characteristic of the user (biometrics); includes fingerprint, iris scan, voice
- Somewhere you are: connected to a specific network or GPS location
Security Partnership
Trust is the #1 priority at Salesforce, which is why Salesforce is promoting a security measure such as multi-factor authentication. However, the responsibility to focus on security does not solely rest on Salesforce’s shoulders. Customers have a responsibility to adopt security, monitor activity, protect data, and stay up-to-date with security updates. Vicasso, as your trusted Salesforce Partner, is here to assist you with the implementation of new security features and provide consultation on best practices.
What MFA Verification Methods does Salesforce currently support?
Salesforce currently supports three groups of verification methods for MFA:
1. Salesforce Authenticator mobile app
2. Third-Party authenticator apps
3. Security keys
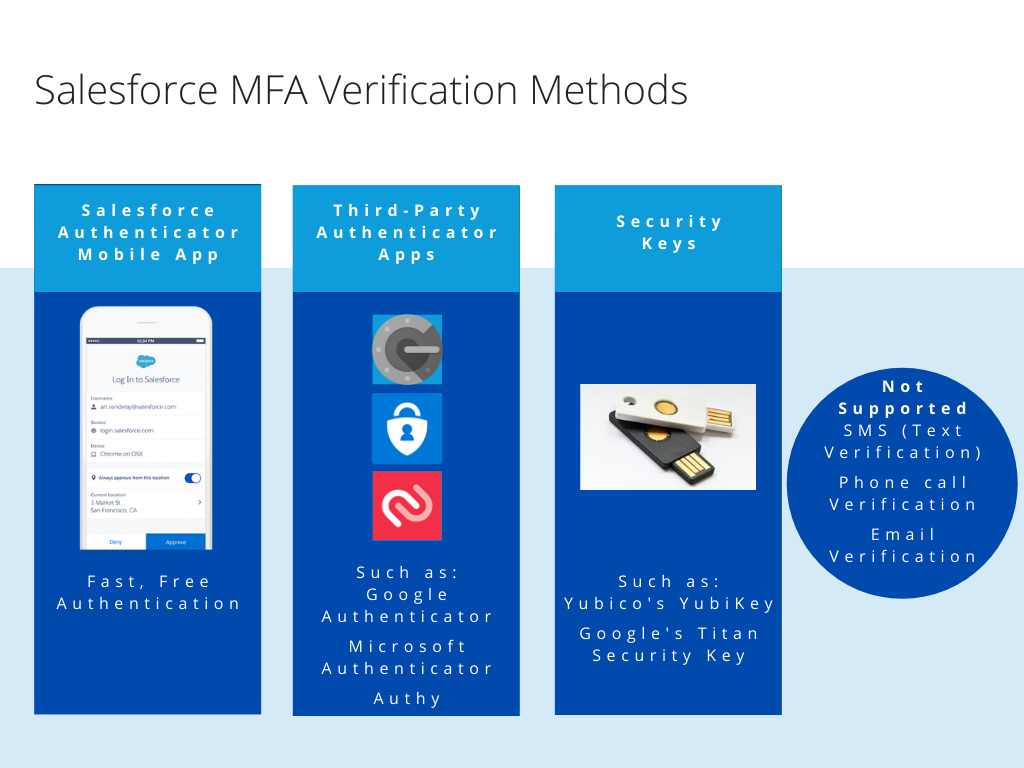
Wait, what about SMS, email, or phone?
Email, SMS text messages, and phone calls aren’t allowed as MFA verification methods because email credentials are more easily compromised, and text messages and phone calls can be intercepted.
Important: While MFA will not be mandated in Salesforce Communities, if you do implement MFA in communities, SMS is an option for verification.
What is Salesforce’s plan?
- Renamed all references to two-factor authentication to multi-factor authentication in permissions and documentation
- Salesforce will begin automatically enabling MFA for users who log in directly to Salesforce products. Admins have the options of disabling this for those who aren’t ready yet.
- You should receive notification before any auto-enablement happens.
- All products built on the Salesforce platform are expected to have MFA auto-enablement between September and October of 2022 with enforcement dates between May and June 2023.
- Introduced Multi-Factor Authentication Assistant in Setup
What do I have to do now?
There are a few options available to you:
- Salesforce offers a MFA Quick Guide for Admins that can be found here and includes steps to enable MFA by product, and steps to register with each verification method.
- And a more in-depth option, How to Roll Out Multi-Factor Authentication, that includes implementation steps, and full details for each of the tasks on the adoption journey.
If you need help in your rollout, you can reach out to your Vicasso Salesforce Expert who can help support the roll out for your team to ensure a smooth transition.
How is this different from when I log in on a different browser?
There are two types of identity verification in Salesforce, service-based and policy-based security. Whenever we log into Salesforce from a different browser or from a new computer, we must provide verification of our identity. This is called service-based identity verification, which is available out-of-the-box. Now, with MFA, you can add a new layer of security on top of it with policy-based identity verification.
- Service-based (device activation)
- Auto enabled for all orgs
- User must provide verification from unrecognized browser or application
- Not considered as part of MFA (insecure)
- Policy-based (MFA)
- Admin enabled
- Multi-factor
What should you keep in mind with MFA?
Here are several things to keep in mind when rolling out MFA.
What are the System Permissions related to MFA for user interface logins?
- Multi-Factor Authentication for User Interface Logins
- Require users to provide an additional verification method in addition to their username and password when logging in to Salesforce orgs.
- Manage Multi-Factor Authentication in User Interface
- Use tools in the user interface to manage and provide user support for multi-factor authentication.
What about MFA for API logins and integrations?
- API logins are not currently part of Salesforce’s mandate to use MFA.
- Any integrations you have in place (such as with an ETL tool like Boomi or Jitterbit) should be implemented with an API Login User.
- API login users can access Salesforce through APIs only and cannot log in normally.
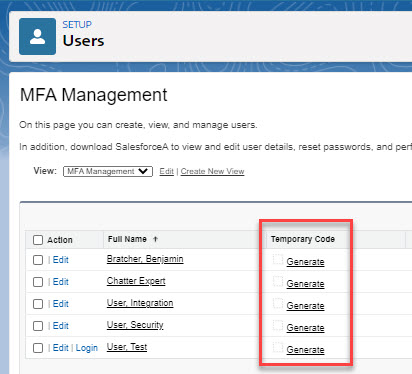
What happens if a user loses or forgets their device?
- Admins can generate temporary verification code that can be set to expire 1 – 24 hours by adding the Temporary Code field to a User list view and clicking “Generate.”
Can Salesforce Authenticator auto-approve logins?
- Salesforce Authenticator can automatically verify identities based on geographic location (phone’s geolocation) or trusted IP addresses.
- You must allow the authentication app to have access to your phone’s geolocation in order for this to work.
Implementation and Activation Steps
The following steps need to be taken in order for MFA to be implemented and activated.
- The Salesforce Admin assigns the permission set with the “Multi-Factor Authentication for User Interface Logins” system permission enabled to users who should be required to use MFA.
- The Salesforce User chooses their MFA Verification Method and connects it when logging in.
- The Salesforce User verifies login through their verification method.
Rollout Plan
It is critical to have a user rollout plan. While the steps to enable MFA are fairly straightforward, it is important to still do the necessary prep work and communication to ensure a seamless rollout. As a resource, we highly recommend using the Multi-Factor Authentication Assistant in Salesforce Setup to walk through the steps to get ready, roll out, and manage MFA.
- Formulate a robust project plan for your MFA rollout and work with your stakeholders to gather and evaluate requirements. Create internal processes for how to offer support with MFA-related issues in the future.
- Communicate the change to MFA early and often to your users so that they are prepared. Using MFA can be disruptive if they are not prepared. Give your users specific steps to follow on how to prepare.
- Salesforce Admin creates a permission set with the system permission “Multi-Factor Authentication for User Interface Logins.”
- Note: The use of permission sets allows you to roll out MFA to individuals or groups of users in phases.
- IMPORTANT: Test MFA in a sandbox environment before rolling it out in production. Make sure to use a Test User so you don’t accidentally lock yourself out of the environment.
- Note: In addition to enabling MFA in production, Salesforce recommends enabling MFA in any sandbox environment that includes production data. If the sandbox has sample data, masked data, or no data, MFA is not necessary.
- Launch a pilot in production with a smaller user group to test MFA.
- The Salesforce Admin continues to monitor any changes to MFA in future Salesforce releases.
How can Vicasso help?
As a Salesforce Partner with a deep knowledge of the platform, we are well-equipped to help you and your organization implement Multi-Factor Authentication and ensure you are following the Salesforce security best practices.
Reach out to us at Vicasso here.
Learn More!
Take advantage of the Salesforce content below to learn more about MFA.
Get More Information About MFA
- Admin Guide to Multi-Factor Authentication
- Salesforce MFA FAQ
- Introduction to Salesforce Authenticator (video)
- Secure Account Access With MFA (webinar)
See More Details About Implementing MFA
- Launch Multi-Factor Authentication (video)
- How to Roll Out Multi-Factor Authentication (help)
- Multi-Factor Authentication (help)
Learn About MFA Using Trailhead



Get More Information on Security
Join the MFA discussion in the MFA – Getting Started Trailblazer Community!


